Permissions
Case Manager users must be members of at least one security group in order to access the Case Manager system.
Security groups are managed at the Security Groups List.
Each security group has a setting for every system permission. Permission settings either allow or don't allow the user to perform a particular action.
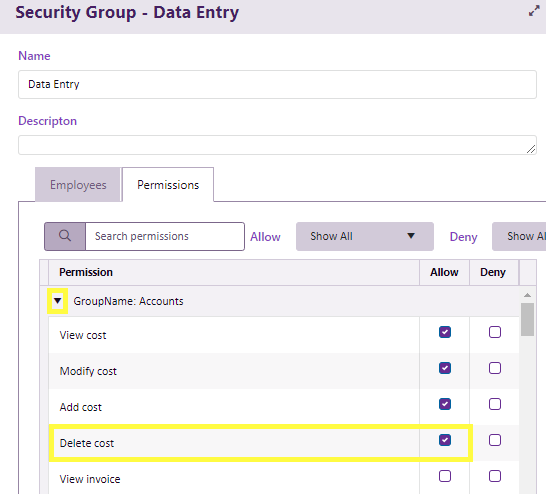
These permissions are quite detailed, for example four independent costs permissions regulate whether a user can add costs, view costs, modify costs and delete costs.
Above the highlighted Delete cost permission has been set to Allow for the Data Entry security group. This means that users who are members of this group can delete costs.
Permissions are grouped by function. You can open and close them by clicking an icon (highlighted above).
| Group | Permissions included |
| Accounts | All accounting functions including costs, invoices, payments and adjustments |
| Administration | Document templates and all reference lists |
| Case Information | Includes case details, contacts, documentation, estimates and case category |
| Custom Field Tabs | View and modify permissions for custom field tabs |
| Custom Fields | View and modify permissions for each custom field |
| Personnel | Employee information |
| Reports | Management reports |
| System Configuration | Includes system options, workflow and custom field creation and modification |
| User Interface | Includes access to general tabs |
Setting permissions
In almost all situations you need only select or un-select the Allow check box for a permission.
If the Allow checkbox is ticked, members of the security group have permission to perform that action. If it is not ticked they not have that permission and are not allowed to perform the action.
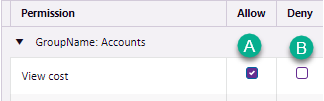
- In the example above users can view costs.
- The Deny check box is only relevant when compiling multiple values for the same permission, see Compilation of permissions below.
Searching and filtering permissions
You can now search the permissions.
Click image to see this feature in action. Click image again to close.
As the animation above shows, enter text in the search box to view only the permissions that contain this text. The example reveals all the cost permissions and shows the settings for each of these in the selected security group (Consultant).
The animation also shows how to filter the list to display only the permissions that do not have Allow ticked.
Finally, it demonstrates how to check whether any Deny settings have been ticked.
Compilation of permissions
Sometimes multiple permission settings must be compiled in order to derive one value for a user.
When a user is a member of multiple security groups, Case Manager evaluates each permission by collecting the values for this permission in all of the user's security groups. These are compiled into one value per permission using two rules:
- If a permission has an Allow value in any of the security groups, this permission is collected into the set of Allows, i.e. allowable actions for the user.
- It is ejected from the set of allowable actions if a Deny value for this permission is located anywhere.
Note that when a value for the permission has been set per user, this value is also collected into the process described above and is subject to the same rules. Thus, it does not override settings for permissions in the user's security group(s).
Be aware that ticking the Deny box for a permission overrides any Allow permission set for a security group (including the System Administrator security group) or for a user.
Thus, the only reason you would ever want to use Deny is when a user is a member of multiple security groups, and you want to prevent certain users having a permission that is allowed in one of those groups.
As explained, the Deny permission overrules any other Allow permissions. So if you were a member of both the Consultant group and the System Administrator group, any deny permissions in the Consultant group would prevent you from performing operations even if they were allowed in the System Administrator group.