Password settings
You may like to start with the introductory video:
It is essential to prevent unauthorised people logging in to your Case Manager system and accessing your data. The system needs to be as secure as possible.
This is particularly important when the login screen is available on the internet.
Case Manager provides a suite of password functions to ensure that user passwords are as strong as possible. These reduce the risk of unauthorised access to the system that can occur when passwords are easily-crackable or if users keep the same passwords too long.
You can also log in to Case Manager using your Microsoft Azure account. This convenient method provides single sign-on (SSO) and the additional security of multi-factor authentication (MFA).
And users logging in to the mobile app can use a passcode that is connected to their login password(s). A number of additional security features apply here, see Mobile app security.
Password settings
To open the password settings select Tools > Options from the main menu.
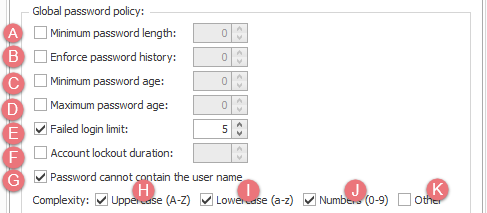
Click the Security tab. You will find the Global password policy section underneath the section for Authentication services.
The settings at A, G and H-K set the complexity of passwords.
B, C and D determine how often they need to be changed.
E and F deter password generators that make multiple login attempts to log in.
- Minimum password length
- Enforce password history
- Minimum password age
This determines how short passwords can be.
The shorter a password the easier it is to guess, which you do not want.
The default length is 8 characters.
You can enter a number between 0 and 16 characters here; 0 means that no password is required.
This sets the number of unique new passwords a user has to create before an old password can be recycled.
This setting prevents users using only one or two passwords that may become known to others as a result of overuse.
The default value is 24 different passwords.
You can enter a number between 0 and 24 here; 0 means that password history checking is disabled.
This sets how many days a user must keep a new password before they can change it. This setting is designed to work with the Enforce password history setting so that users cannot subvert the setting (at B) by quickly resetting their password the required number of times and then changing back to their old passwords.
The default value is 0.
You can enter a number between 0 and 9; 0 means that users can immediately change a new password.
- Password cannot contain the user name
This setting prevents the use of a very insecure password that is simply the user's name.
Such a password is undesirable because a hacker only needs to know the user's name to gain access to the system.
By default this option is set on.
The four password character complexity options ensure that a password must contain one or more characters from the following character sets:
- English uppercase characters (A - Z),
- English lowercase characters (a - z),
- Digits (0 - 9),
- Non-alphanumeric characters, for example: !, $, #, or %.
The use of these characters in a password increases its complexity and makes it harder to crack.
Any changes to the password policy options above are only enforced when a new password is entered. Existing passwords that do not meet an updated password policy remain valid, which is intentional. If a change to the policy needs to be applied to all users, you can force a password reset for everyone at their next login, see Forced password changes.
- Maximum password age
- Failed login limit
- Failed login lockout time
This sets how many days a password can be used before the user is required to change it.
If users have the same password for a long time the risk increases that it could become known by someone else. However you need to strike a balance with this setting, because if users have to change passwords too often they may start using simpler, more easily guessable passwords, which defeats the purpose.
The default value is 42 days.
You can enter a number between 0 and 99; 0 means that user passwords never expire.
This sets how many failed logins are allowed before the user is locked out for a specified time.
The setting stops the use of random password generators that automatically submit multiple passwords, one at a time.
The default value is 5 attempts.
You can enter a number between 0 and 9; 0 means there is no limit.
This sets how long a user is locked out after exceeding the failed login limit.
The setting also aims to stop random password generators.
The default value is 5 minutes.
You can enter a value between 0 and 24 hours; 0 means that after one failed login they are locked out indefinitely.